Windows内核实验:平行进程
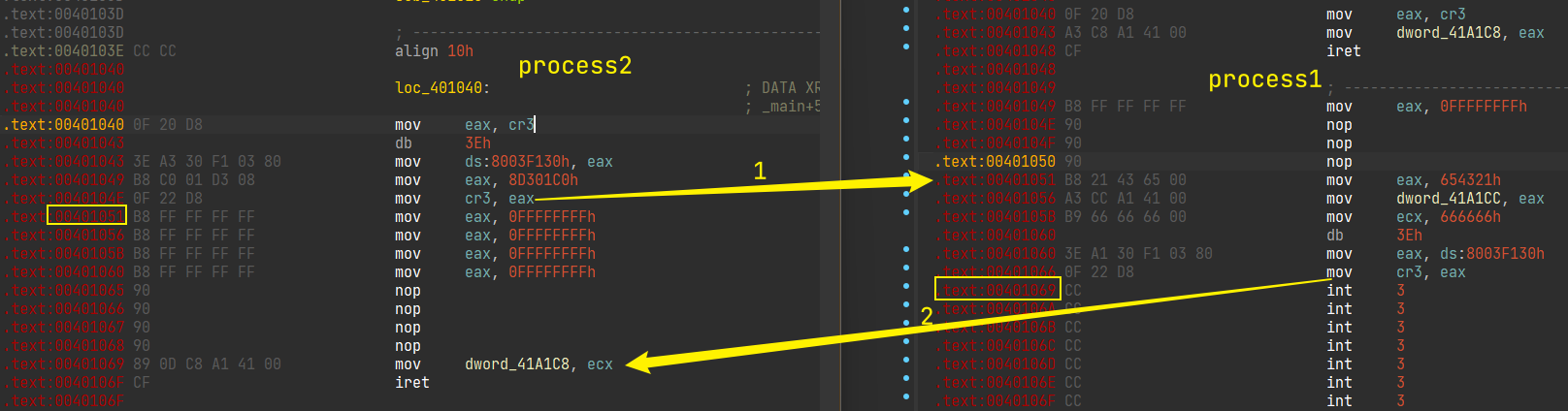
主要思想就是A进程在切换B进程的cr3后,将B进程中当前A进程的eip所指向的地址构造为要想要执行指令
实验现象
process1.c
#include <stdio.h>
#include <stdlib.h>
#include <windows.h>
DWORD g_cr3;
DWORD g_flag;
void __declspec(naked) IdtEntry() {
__asm {
mov eax, cr3
mov g_cr3, eax
iretd
mov eax, 0xffffffff
nop
nop
nop
mov eax,0x654321
mov g_flag,eax
mov ecx,0x666666
mov eax,ds:[0x8003f130]
mov cr3,eax
}
void interrupt() {
__asm {
int 0x20
}
}
int main() {
if (0x401040 != IdtEntry) {
printf("Idtentry address wrong");
system("pause");
exit(-1);
}
interrupt();
while (TRUE) {
printf("cr3:0x%x\tg_flag:0x%x\n", g_cr3, g_flag);
Sleep(1000);
}
system("pause");
}
|
process2.c
#include <stdio.h>
#include <stdlib.h>
#include <windows.h>
DWORD g_num;
void __declspec(naked) IdtEntry() {
__asm {
mov eax, cr3
mov ds:[0x8003f130],eax
mov eax, 0x8d301c0
mov cr3, eax
mov eax, 0xffffffff
mov eax, 0xffffffff
mov eax, 0xffffffff
mov eax, 0xffffffff
nop
nop
nop
nop
mov g_num, ecx
iretd
}
}
void interrupt() {
__asm {
int 0x20
}
}
int main() {
if (0x401040 != IdtEntry) {
printf("Idtentry address wrong");
system("pause");
exit(-1);
}
interrupt();
printf("cr3:0x%x\n",g_num);
system("pause");
}
|
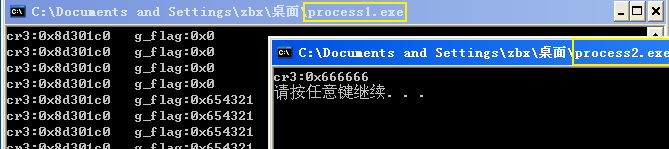
实验现象就是先运行process1,打印cr3后gflag为0,运行process2后gfalg被修改为0x654321,且process2的g_num被修改为0x66666
分析