#include <stdio.h>
#include <stdlib.h>
#include <windows.h>
#define T_ERRNO 0x8003f250
#define T_EIP 0x8003f254
#define T_CR3 0x8003f258
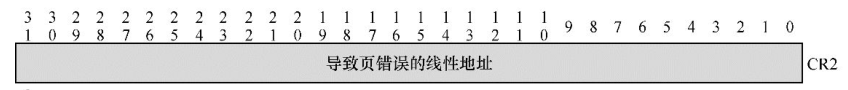
#define T_CR2 0x8003f25c
void JmpTarget();
char* p = (char*)0x8003f130;
size_t i;
void __declspec(naked) IdtEntry() {
for (i = 0; i < 0x100; i++) {
*p = ((char*)JmpTarget)[i];
p++;
}
__asm {
mov eax, cr0
and eax, not 0x10000
mov cr0, eax
mov al,0x68
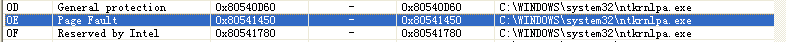
mov ds:[0x80541450],al
mov dword ptr ds:[0x80541451],0x8003f130
mov al,0xc3
mov ds:[0x80541455],al
mov eax,0xffffffff
mov ds:[T_CR3],eax
xor eax,eax
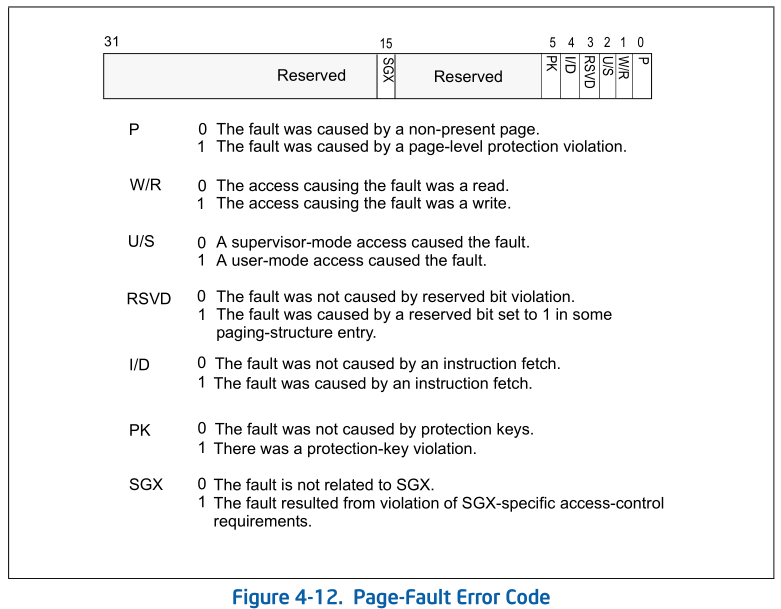
mov ds:[T_ERRNO],eax
mov ds:[T_CR2],eax
mov ds:[T_EIP],eax
mov eax, cr0
or eax, 0x10000
mov cr0, eax
iretd
}
}
void __declspec(naked) JmpTarget() {
__asm {
push eax
mov eax,cr3
cmp eax,ds:[T_CR3]
jnz end
mov eax,ss:[esp+4]
mov ds:[T_ERRNO],eax
mov eax,ss:[esp+8]
mov ds:[T_EIP],eax
mov eax,cr2
mov ds:[T_CR2],eax
end:
pop eax
mov word ptr[esp + 2], 0
push 0x80541457
ret
}
}
void interrupt() {
__asm {
int 0x20
}
}
int main() {
if (0x401040 != IdtEntry) {
printf("IdtRntry address wrong");
system("pause");
exit(-1);
}
interrupt();
system("pause");
}
|