2023 Securinets CTF Quals
Admin Service
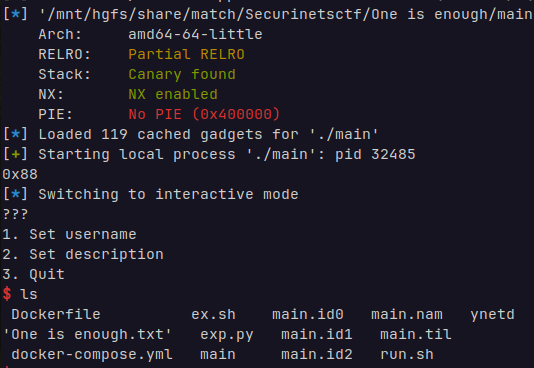
grxer@Ubantu20 ~/s/m/S/A/togive> checksec ./services |
开了沙箱
grxer@Ubantu20 ~/s/m/S/A/togive> seccomp-tools dump ./services |
readChat可以跳出目录利用/proc/self/maps泄露基地址,updateConfig可以无限越界写
from pwn import * |
ret2libc
grxer@Ubuntu22 ~/s/m/S/r/togive> checksec main |
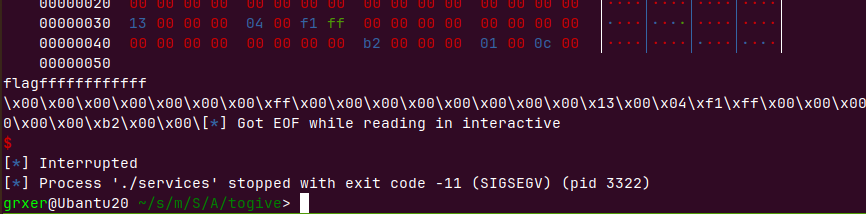
栈溢出,但是通过ecx寄存器把原来的esp保存到栈上,再常规提升堆栈,导致ret和ebp直接有一段距离,找到ret需要栈上之前保存的esp值,所以不能覆盖ret
可以利用gets把‘\n’截断为\x00覆盖存放在栈上的esp的低位为00,有很大机率将esp提升到我们gets输入的栈空间,payload前面用ret填充后面写top链即可
.text:080491D3 8D 4C 24 04 lea ecx, [esp+4] |
from pwn import * |
One is enough
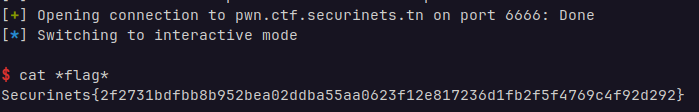
[*] '/mnt/hgfs/share/match/Securinetsctf/One is enough/main' |
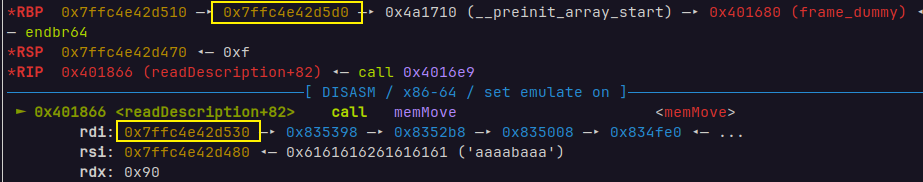
readInput里有一个字节的溢出,所以在两个功能函数都能修改保存到栈上的main函数的rbp,静态编译的程序里面有syscall的gadget,所以就可以控制rbp在main返回时利用rop
断点下到 readDescription的memMove,只要main的rbp和读入数据的栈地址只有最后一位不同就行,大概也就16种可能,总有机会会爆破到
from pwn import * |