2023 蓝帽杯
takeway
libc2.31的uaf,可以直接覆盖tcache的next来任意地址申请堆块
思路就是通过uaf和tcache的key泄露出堆地址就可以获得我们申请的堆地址,申请到0x4040A0处的堆管理结构指针后就可以改他的值为我们可控的堆,提前把可控堆里的内容改完free的got edit功能时就可以泄露基地址和修改freegot为system
from pwn import * |
heapSpary
Create堆里是一次申请16个堆,堆块的顺序是乱的,在往堆写数据时没有限制大小可以无限堆溢出
Action是一个后门
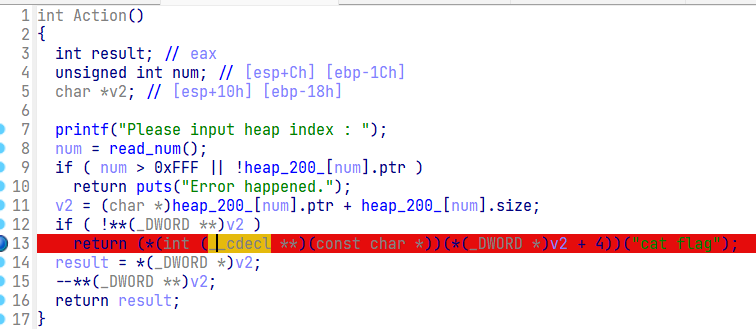
我们需要堆+堆大小处存放的地址的前四个字节为0,后四个字节为system就可以拿到flag
*(void*)(heap_ptr+size)------>0 |
泄露libc,虽然有堆溢出,但是却在输入后有\x00截断常规unsortedbin泄露就失效了,但是Create堆时flag是往堆+堆size位置写入四个字节可以覆盖掉这个/x00
比如我们申请creat大小为1,这个值只会覆盖unsorted堆的fd及bk的第一个bit,如果bk此时指向是unsortedbin就可以泄露出libc,所以可以利用创建大小为1的堆块切割unsortedbin来泄露libc
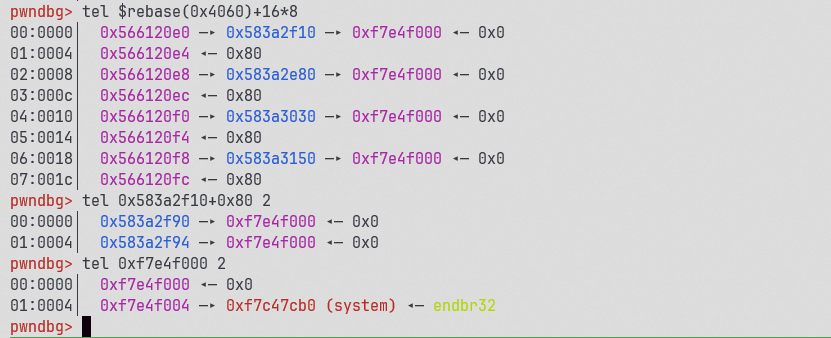
有了libc就是需要布置满足后门的堆块,可以申请0x20000大小的堆来mmap内存,但是这道题开了pie,mmap的位置是随机的,但是随机的不多,程序一次申请16个来堆喷,基本上位置都在libc下面偏移0x24f000处得到
利用mmap堆喷在libc下面布置大量的p32(0)+p32(systme),我们把这个位置叫slide
再利用creat堆溢出往堆上写大量的p32(slide),由于creat是乱序的,当出现下面的情况时
heapA+10,heapA |
heapA堆溢出大量的p32(slide)就可以覆盖掉heapA+10堆块,就可以绕过Create里Which flag do you want?的赋值
from pwn import * |